Cybersecurity
The encryption solution that prevents anyone from accessing your confidential data
IPSIP - March 2024
Today, it is more important than ever to protect information systems. We must comply with confidentiality standards and protect ourselves against cyberattacks, which can lead to massive data leaks or paralyse our information systems.
In this article, we will discuss one of the best practices to adopt right now: the encryption of confidential data.
How does this solution make data unreadable to ensure its confidentiality?
What is data encryption?
Data encryption involves scrambling data into a secret code that can only be unlocked with a unique digital key. There are two main methods of encryption:
– Symmetric encryption, in which messages are encrypted and decrypted using the same key. This is the oldest method of encryption. Evidence of its use can be found in Ancient Egypt.
– Asymmetric encryption, considered the most secure method because it is very difficult to corrupt, as explained below.
““Key management is a crucial process in the configuration of a cryptographic system, and becomes even more complex as the volume and distribution of data and the number of actors involved are significant.” – CNIL (French Data Protection Authority)
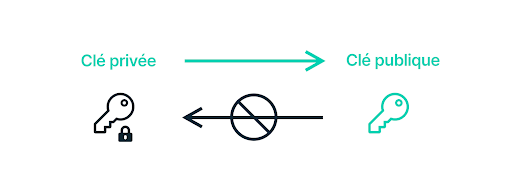
Public keys and private keys: what are they?
Asymmetric cryptography is based on a two-key model, a public key and a private key, often represented by a lock (public key), with the private key opening the lock. The public key is only used to encrypt the document, while the private key is used to decrypt it.
The owner of the private key can retrieve the public key to access their private data, but the reverse is impossible because the principle is based on complex mathematical operations.
Credits : Kristy Moreland – Ledger Academy
Is data encryption alone sufficient to protect data?
Now that we know that data encryption is one of the essential practices for protecting the confidentiality of sensitive information, let's take a look at how bad behaviour can undermine its effectiveness.
How can you be sure that the ‘secrets’ are properly encrypted?
Secrets are a specific term in cybersecurity used to refer to sensitive data that must not be disclosed under any circumstances, as this could harm the company's business activities. Examples include passwords, API certificates and digital certificates.
One way to encrypt secrets is to use base64 encoding. This is an algorithm that converts text into a string of characters consisting of letters, numbers and symbols.
For example:
Password: 123456
Encoded in base64 : VGhpcyBpcyBhIhRlc482c2Q
However, this encoding is not a secure method because if someone has access to the base64 encryption code, using tools or software, they can decrypt the secret message and read it. It is therefore recommended to use a more robust algorithm such as asymmetric encryption, as discussed above.
The dangers of entrusting secret keys to third-party service providers.
When storing data in a public cloud, we use keys that are managed by default by the cloud provider. For example, you can use a virtual safe, known as a vault. Often provided by a cloud provider or external service provider, this safe is presented as a complementary solution. However, it is important to note the disadvantages of this method:
- Who has access to your data ?
- Are some accesses unauthorised?
- Are data protection regulations being complied with?
Let's take Microsoft Azure as an example:
In November 2023, Microsoft revealed that a group of hackers known as Nobelium had targeted customers using Microsoft Azure.
Consequences of the attack:
Vol de données sensibles :
Les pirates ont pu accéder à des données sensibles stockées dans Azure, y compris des noms d’utilisateur, des mots de passe and jetons d’authentification.
Compromise of computer systems:
They were able to use the compromised accounts to access customers' computer systems and execute malicious commands.
Disruption of operations:
The attack caused service outages and significant slowdowns.
How can encryption key security be strengthened?
Encryption key management is essential for the security of sensitive data. Not to mention compliance with privacy rights under the General Data Protection Regulation (GDPR), which must be taken into account in this management.
You can opt for an HSM (Hardware Security Module) device, which will allow us to store your cryptographic keys and thus protect our secrets against data leaks or malicious actions. HSM devices offer a high level of security for the protection of cryptographic keys. They are essential for applications that require maximum protection of sensitive data.
Here are some examples of how HSM devices can be used:
- Data encryption to protect against unauthorised access, as we have seen
- Digital signature for signing documents and transactions. This ensures the authenticity and integrity of data.
- Required authentication of users and devices to protect IT systems.
You then have the option of purchasing a local HSM, which is usually physically protected, that you can deploy within your own infrastructure. However, this method is somewhat costly and requires complete and permanent internal control.
Otherwise, it is often more advantageous to use a Cloud HSM box provider. The HSM will be based on a cloud provided as a service, offering simplicity and agility at a cost tailored to your needs.
How does DuoKey innovate to secure encryption key management and strengthen your cybersecurity?
Are you wondering how to implement secure encryption key management practices and who to call on for help?
 DuoKey is an innovative solution that allows you to manage your encryption keys securely, ensuring maximum data protection while complying with regulations and compliance rules (GDPR, HIPAA, etc.).
DuoKey is an innovative solution that allows you to manage your encryption keys securely, ensuring maximum data protection while complying with regulations and compliance rules (GDPR, HIPAA, etc.).
Specific features:
DuoKey offers a key management solution based on MPC (Multi-Party Computation) technology, a cryptographic method that allows the key to be split into several parts and stored in separate locations. The advantage of this method is that no HSM is required. A piece of the key can be stored in any cloud. Even if that cloud is hacked, no one will be able to do anything with a piece of the key.

Credits: DuoKey
DuoKey helps you manage your encryption keys securely and efficiently, whether you want to store your keys in a local HSM, an HSM cloud, or MPC (Multi-party Computation).
With a solution like DuoKey, you can take control of the confidentiality of your secret data. You will have complete control over access to your data as well as key storage.
Key takeaways
Protecting sensitive data in today's application environments is a complex but crucial task.
Encryption, although fundamental, requires a thoughtful approach and, to go further, consideration of implementing dual encryption solutions such as DuoKey. These offer additional protection while ensuring total control over your encryption keys.
Any methods chosen to ensure the security of your keys should be guided by your specific security needs.
Stay vigilant, adapt to technological developments, and make data security a constant priority. Your business, and your customers' trust, will be the direct beneficiaries.
Contact our specialists, they will work with you to assess your data protection needs.
